GDPR Compliance
Dataflow and Storage
The iSentry platform is regarded from a GDPR perspective as a “Data Processor” and not a “Data Controller”. As such all data is processed within the client environment with no real time interaction, extrenal access or data feedback into the iSentry system. The below will explain the technical specifics within a Milestone implementation.
The iSentry platform is fully integrated into the Milestone XProtect Video Management System (VMS), which allows iSentry to process video without the requirement to store video data, since all video data is managed by the Milestone VMS.
When video is required for display in the Client interface, for example when an iSentry alert has been generated, the VMS performs this function as per the standard VMS procedure.
On a high level, Video data is consumed from the VMS and alert data is pushed back into the VMS, with no data leaving this environment.
The diagram below provides a full overview of data processing and storage processes for the Milestone integrated iSentry system.
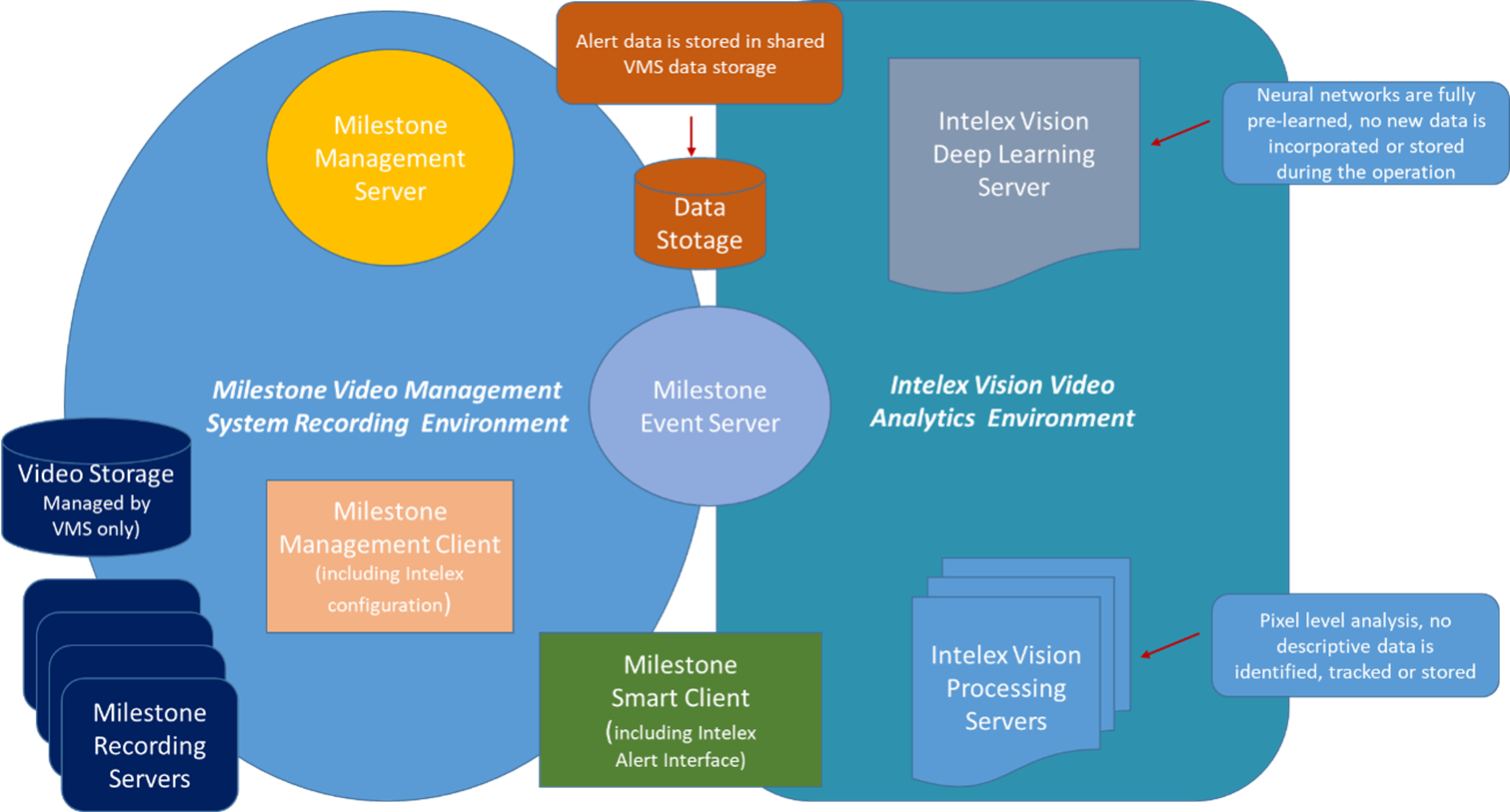
Video Storage
All video storage is managed by the Milestone VMS.
Data Storage
iSentry system data is jointly stored with the VMS data in a SQL server database.
Communications
All iSentry communications are based on Milestone standard internal communications mechanisms. This allows iSentry to use existing security and excrytption protocols as used by the VMS itself.
iSentry Unusual Behaviour and TREX Processing
Live video is consumed and processed directly from the Milestone VMS, and no private data is known to the system since only pixels and groups of pixels are identified and tracked throughout a scene.
iSentry Deep Learning (Object Classification)
The iSentry Deep Learning system classifies the source object type responsible for an iSentry alert through fully pre-learned neural networks. These networks are trained on generic and synthetic data, and do not contain any private data. Furthermore, no further learning takes place during production, and no learning feedback is available.
iSentry Rule Processing
The iSentry rule system aims to reduce alert volume by applying pre-configured logic to alerts. Alerts that pass rules checking will be displayed to operators for further analysis. It is the operator at the Control Centre who will finally determine if an unusual behaviour alert must be dismissed, alarmed as security threat or treated as another kind of alert that may require a different response mechanism, for instance medical attention (for example, call an ambulance)
Configuration
The iSentry configuration interfaces are embedded in the (VMS) Milestone Management Client Interface.
Operations
The iSentry alert interfaces are fully embedded in the Milestone Smart Client, leveraging the Milestone security and encryption technologies.
This policy was updated as of January 2022
-- POLICY ENDS --
